The Evolution of Ransomware: Multi-stage Attacks and RaaS
Merkle Science

The Evolution of Ransomware: Multi-stage Attacks and RaaS
This is the third article in a series that examines the rise of ransomware, which is critical for crypto businesses to understand in order to avoid processing associated transactions involving fraudulent addresses. Unknowingly facilitating money laundering or other illegal activities can result in regulatory sanctions, legal penalties, and reputational damage.
To read the first article in the series,’ How Crypto Has Revolutionized the Ransomware Game’ and the second article, ’Inspiring industry action: How the FATF believes we can counter ransomware’
To avoid these risks, crypto businesses must be aware of the threats and take measures to prevent ransomware attacks and stop the flow of ransom funds. By doing so, they can operate within regulatory bounds and safeguard both their customers and their business.
As we have seen in our first article, ransomware is devastating to enterprises and individuals. Through a wide variety of ransomware attacks and techniques, including everything from lockers and leakware to encryption and scareware, attackers are often able to walk away with large ransom sums, sent to them in cryptocurrency. When enterprises comply with ransom payments, it naturally encourages attackers to not only continue with similar attacks but develop even more sophisticated practices. Several attacks in particular - ransomware as a service, triple extortion, and quadruple extortion - represent the pinnacle of these cybercrimes. Therefore, paying close attention to these highest-level attacks is important for several reasons.

The Escalation of Ransomware: Understanding Triple and Quadruple Extortion Attacks
In recent years, we've seen the emergence of triple and quadruple extortion attacks, which pose an even greater threat to individuals and organizations. To defend against these evolving threats, it's essential to understand the different types of ransomware attacks and take necessary precautions to protect sensitive data and systems. In this chapter, we'll explore the dangers of triple and quadruple extortion, and provide practical tips for safeguarding against these sophisticated attacks.
In Triple Extortion, hackers not only lock the victim's data but also threaten to expose it to the public. Quadruple Extortion takes it one step further by launching a DOS attack or harassing the organization's partners, customers, and stakeholders. These attacks are particularly effective as they target multiple stakeholders through a single attack vector.
The Vastaamo Clinic attack is an example of the devastating impact of triple extortion. After stealing data from the clinic, hackers demanded payment from the clinic and later targeted individual patients, demanding payment in exchange for not exposing their therapy notes.
Decoding Ransomware As a Service Model
As professionals in the industry, we are all familiar with the concept of software as a service. With SaaS, software providers extend access to their products on a recurring basis, usually monthly, and via subscription. This model enables enterprise clients to grow more sustainably since they don’t have to make lump-sum payments and pay in lockstep with the value they get from the product.
Criminals are bringing the flexibility of SaaS to ransomware via ransomware as a service (RaaS). Like with SaaS, there is a ransomware provider, who advertises their SaaS via the dark web. They provide similar product-level information as legitimate companies, such as user reviews, bundle offers, and even community forums. This enables non-technical attackers to choose the best ransomware for their particular needs.
How RaaS Works: A Step-by-Step Guide
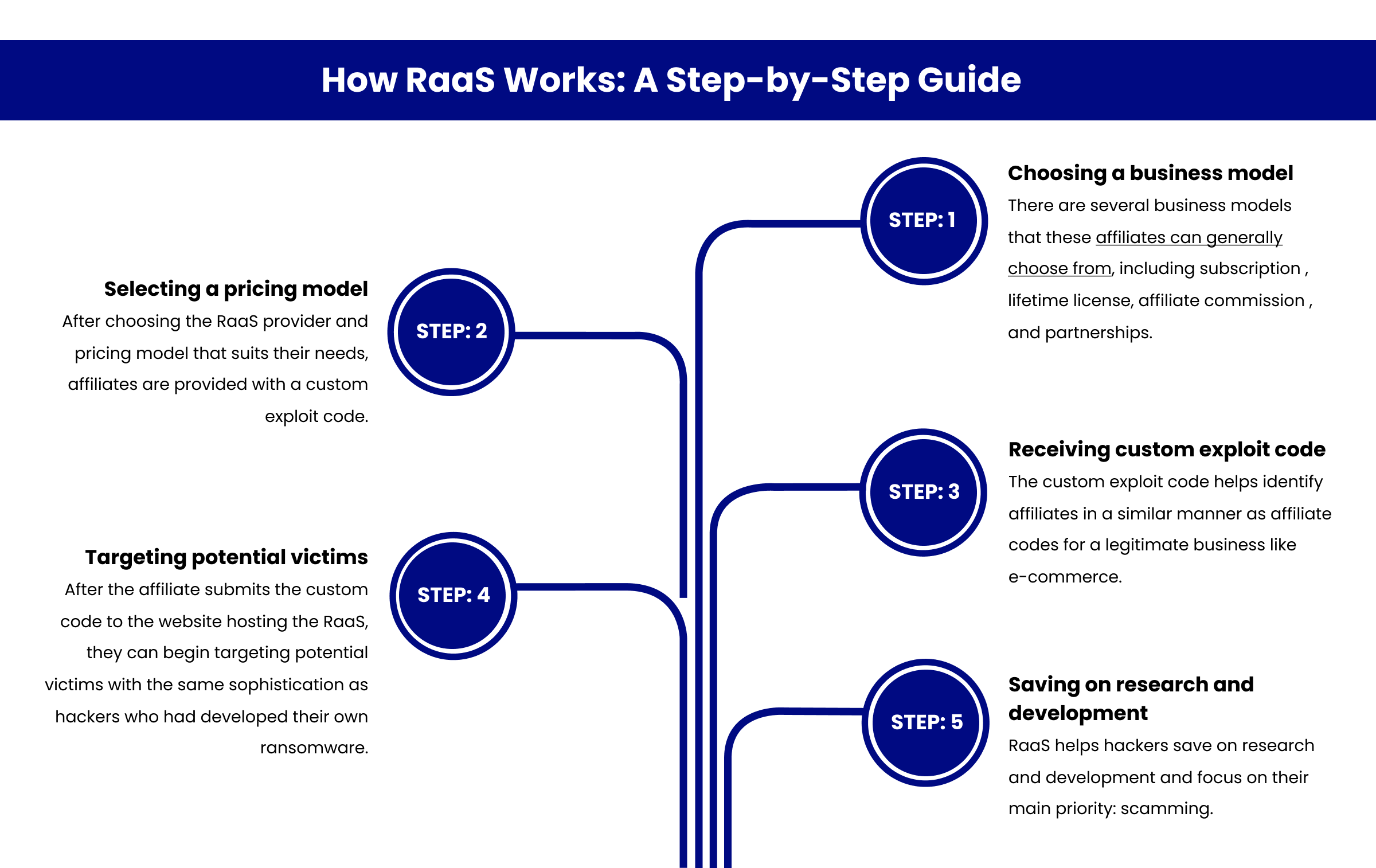
Ultimately, to protect against ransomware attacks, individuals and enterprises should focus on the basics, such as backing up all files in the cloud, running antivirus software, avoiding suspicious links and sites, and ignoring any demands for payment from attackers. In the end, the key to protection against ransomware is to have a comprehensive business continuity plan in place so that organizations can maintain operations in the event of an attack.
Using Blockchain Analytics to Track Ransomware Payments
However, using crypto to facilitate ransom payments, can act as a double-edged sword. For instance, if the ransom is paid in Bitcoin, blockchain analytics companies can trace the transaction on the public bitcoin blockchain, which can lead them to the attached bitcoin address. Blockchain analytics is be a valuable tool in combatting ransomware attacks by tracing the movement of funds through the blockchain.
Blockchain analytics providers may also aggregate off-chain - data to identify senders and receivers of the funds. To achieve this, analytics analyze historical blockchain data, combined with knowledge of good and bad actors and techniques, to detect transaction patterns. This makes it possible to identify the blockchain addresses of illicit actors and provides a critical opportunity to track illicit funds.

How Does Merkle Science Enable Detection of Ransomware-Related Activity
Compass, our core platform, is a blockchain wallet and transaction monitoring system, designed to help businesses track fund movements in real time in case their clients are sending them funds from sanctioned entities, darknet marketplaces, or ransomware accounts to name a few.
Compass provides powerful capabilities for tracking the flow of funds associated with ransomware payments. It supports two types of rules - the source of funds and behavior-based rules - that can be customized to detect any suspicious activity related to ransomware payments.
When screening an address, Compass analyzes the entire transactional history of the address to determine whether any rules have been violated. If a rule has been violated, Compass will raise an appropriate alert, enabling analysts to quickly identify and investigate any potential ransomware-related activity.
Moreover, Compass supports continuous transaction monitoring, where any subsequent transactions conducted by a monitored address will cause the address to be re-screened for any potential rule violations. This allows for real-time detection of suspicious activity and quick response to combat ransomware attacks.
Source of Funds Rule
Compass’ source of funds rules operate by screening an address as well as every address it has ever transacted with, and runs those addresses through our proprietary database, which includes addresses sanctioned by government authorities, to identify if the address itself or any address it had transacted with in the past is linked to illicit activity. These source of funds rules can be created to raise alerts at a single hop or at multiple hops, thereby allowing the user to receive different alerts depending on the proximity of the risk to the address screened.
The source of funds rules can be customized to specifically target ransomware-related activity. For example, Compass can create customized rules to detect and flag addresses associated with known ransomware variants.s. Additionally, thresholds can be set to trigger an alert when a transaction exceeds a certain amount or when a certain number of transactions occur within a specific time frame. This can help identify large or rapid movements of funds, which are often indicators of ransomware activity.
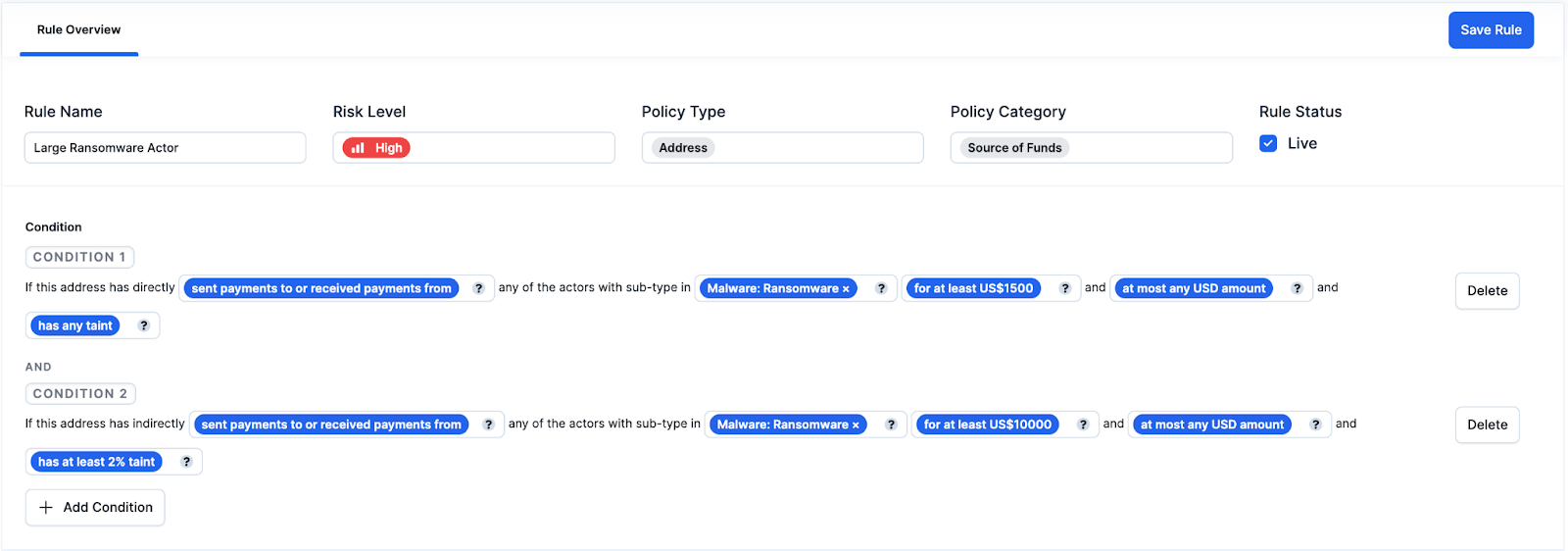
An example of a source of fund rule might state:
“If this address has directly [sent payments to or received payments from] any of the actors with type [Malware: Ransomware] [for at least US$1500] and [has any taint]” can be classified as a HIGH RISK. Conversely, if this address has indirectly [sent payments to or received payments from] any of the actors with type [Malware: Ransomware] [for at least US$10,000] and [has at least 2% taint] will be considered high risk.
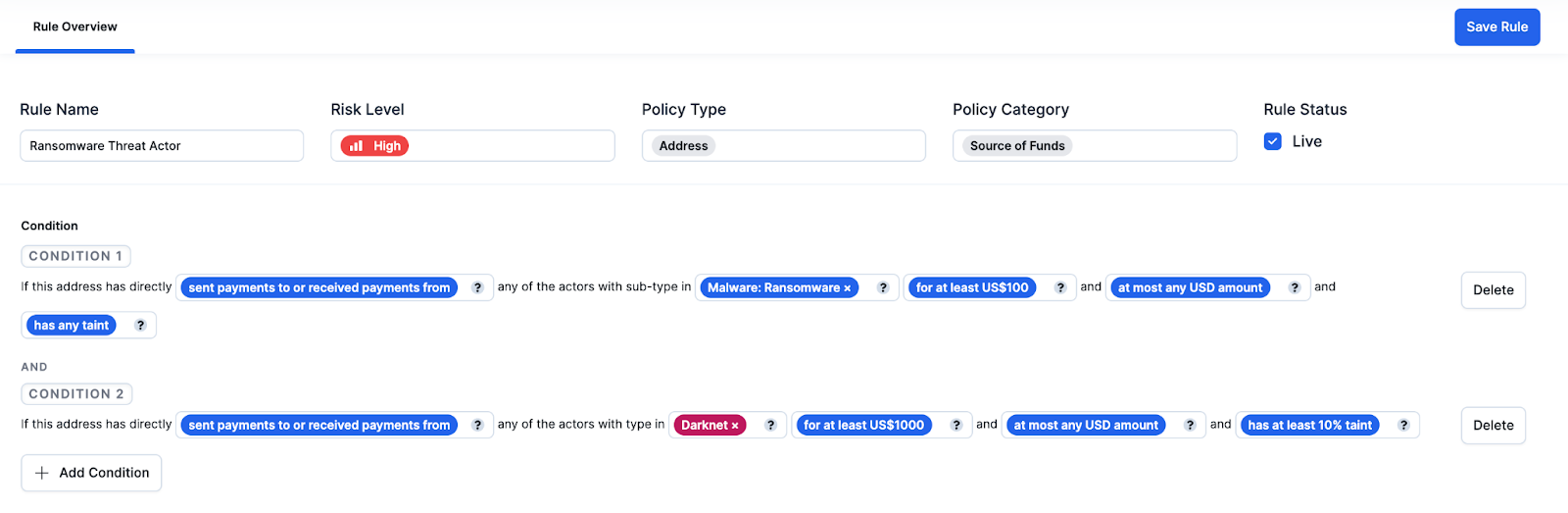
Another example of a source of fund rule might state:
“If this address has directly [sent payments to or received payments from] any of the actors with type [Malware: Ransomware] [for at least US$100] and [has any taint]” can be classified as a HIGH RISK. Conversely, if this address has indirectly [sent payments to or received payments from] any of the actors with type [Darknet] [for at least US$10,000] and [has at least 2% taint] will be considered high risk.
Behavior-Based Rules
Compass’s behavior-based rules go beyond just identifying where funds have come or gone but analyze an address’s transactional activity and raise an alert if the behavior is suspicious. As industry participants are likely aware, it is very easy for criminals to create new addresses in order to hide the source of funds. Hence this was implemented as a solution to the problem: How do you detect potentially criminal wallets that are not listed on a criminal database or the blacklist list?
Behavior-based rules are a unique feature that are present in majority of other blockchain monitoring tools but is something that is increasingly expected by regulators. Instead of having to use two separate tools for wallet screening and transaction monitoring, Compass allows for both to be conducted on a single platform allowing for more accurate and robust monitoring.
Merkle Science’s behavior analytics-driven transaction monitoring tool can with a high accuracy identify the proceeds of ransomware payments making it harder for ransomware actors to launder the proceeds of their illegal activity.
In the Colonial Pipeline Case , Darkside ransomware funds had all the signs of being related to crime. For example, as in most ransomware cases, the criminals created a new address to demand ransom, and then a large amount of crypto was transferred within hours of its creation. Merkle Science’s behavior-based rule engine leverages deep learning-based behavior analysis models to detect addresses associated with criminals that leverage sophisticated techniques, such as using ‘young addresses,’ to bypass detection by traditional blockchain analytics platforms. Merkle Science allows you to set up custom parameters to flag ‘young addresses’ that start to send or receive large funds within a few days or hours of their creation and are not listed in any sanction list for criminal activity nor associated with any known criminal entity.
Merkle Science’s Analysis of Colonial Pipeline Attacks
Let’s take a look at a few examples of how criminals conceal their activities and how Merkle Science can aid your firm in detecting such sophisticated behavior. Attacks involving Colonial Pipeline have brought ransomware to the forefront. In the Colonial Pipeline ransomware incident, an attacker known as DarkSide hijacked the company’s network.
The attackers then demanded ransom in exchange for an encryption key to gain access to the network. The attackers shared a newly created Bitcoin address for ransom. Within two days of the attack, the attackers received over USD $4.4 million in ransom from the Colonial Pipeline on 9 May 2021.
Since DarkSide operates as “ransomware as a service,” the attackers made a payment to DarkSide in return for the use of ransomware tools and moved the funds to the addresses owned by DarkSide ransomware developers.
The first incoming transaction was USD 1 and then the next transaction was USD $4,433,726. Post this, 63.79 BTC (approximately USD $2.3 million) was moved from the wallets controlled by DarkSide developers back to the attackers. On 7th June 2021, the FBI got access to the address controlled by the attackers and recovered 63.70 BTC (USD $2.3 million).
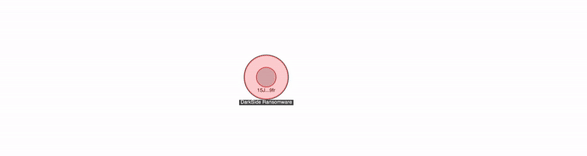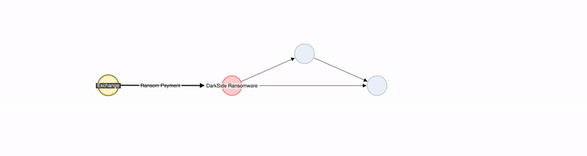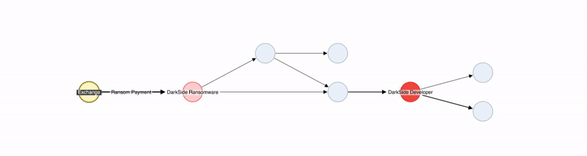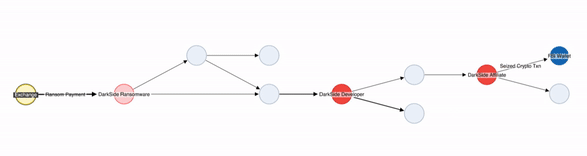
Image Description - Tracing ransom sent by Colonial Pipeline on Crypto Forensics Tool
Though the FBI later recovered most of the funds from the hack within a month, in an ideal scenario, Gemini, the recipient exchange of the funds, should have been able to freeze the funds as soon they received them without interference from the FBI. However, it appears that Gemini’s blockchain analytics provider missed flagging this transaction given that it wasn’t associated with a blacklist/database as it is common with traditional blockchain analytics providers that rely on sanction lists and databases.
Staying Ahead of Crypto-Ransomware Payments with Merkle Science's Tracker
As crypto-ransomware attacks grow in complexity and frequency, organizations need advanced investigative tools to trace these transactions. Merkle Science's 'Tracker' presents an advanced solution in the realm of blockchain intelligence, providing forensic insights into cryptocurrency wallet activity and transactional flows. By visualizing the pathways of crypto assets across known entities and wallets, Tracker disentangles the often complex web spun by cyber criminals.
Along with its advanced auto-investigation features and smart alerts, Tracker seamlessly enables cross-chain investigations, expanding the spectrum of traceability. These capabilities, combined with our team of seasoned investigators, ensure that organizations can accurately track, analyze, and respond to crypto-ransomware payments


